Hi everyone
I’d like to install Ghost on a VPS from DigitalOcean. Is there a ‘noob’ guide covering everything from start to finish available somewhere? Their Ocean cast is not so clear.
Hi everyone
I’d like to install Ghost on a VPS from DigitalOcean. Is there a ‘noob’ guide covering everything from start to finish available somewhere? Their Ocean cast is not so clear.
Instructions are in the official docs, there’s also a link to the 1-click DigitalOcean setup which is super simple to get started with.
I’ve successfully installed Ghost with the 1-click DigitalOcean but I got an outgoing DDoS attack a couple of days later… I was hoping to find a full tutorial which explains how to prevent that as well.
I have another question, how do I get access to /content/themes/casper/post.hbs? I would like to modify post.hbs.
It’s not something we’ve heard about before so you won’t find any tutorial which explains it. You’ll need to investigate how/why such an alert was triggered. How do you know there was an outgoing DDoS attach?
I have another question, how do I get access to /content/themes/casper/post.hbs? I would like to modify post.hbs.
After logging in as an admin, click the Design link in the left-hand navigation. On that screen you can download and upload themes.
There are a few ways to fight against DDOS:
A search on google will yield quite a lot of useful results.
@dsecareanu those are useful resources for incoming DDoS attacks but @Astro mentioned an outgoing DDoS attack which suggests that some network requests originating from the VPS were seen as an attack. That’s why it would be useful to know how that was detected and any other information about what traffic was seen as being an attack.
Ah, sorry, missed the “outgoing” part ![]() .
.
Well, the issues probably stem from an improper VPS security (some help about it here):
Cleaning up a hacked server can be a very tedious job, you would probably be better of just backing up your data and making a new server that you properly secure as indicated above.
@dsecareanu, @Astro mentioned this was after using the 1-click DO install which should already be pretty locked down, I’m trying to determine if there’s a problem there so that we can address it with DO 
First port of call is working out where the DDoS notification came from and if there are any details about the type of traffic that triggered it. We have nothing to go on at the moment, other than a 1-click install was created and a notification received a few days later. @Astro did you set up anything else on the VPS or use other services to watch network traffic?
I have used the 1-click Ghost 2 install on Digital Ocean. Works like a charm.
Ask others have suggested how you determined that your server was engaged in outdoing DDoS attack.
Hi @Kevin, @khurtwilliams
Here’s the email I received from DigitalOcean: 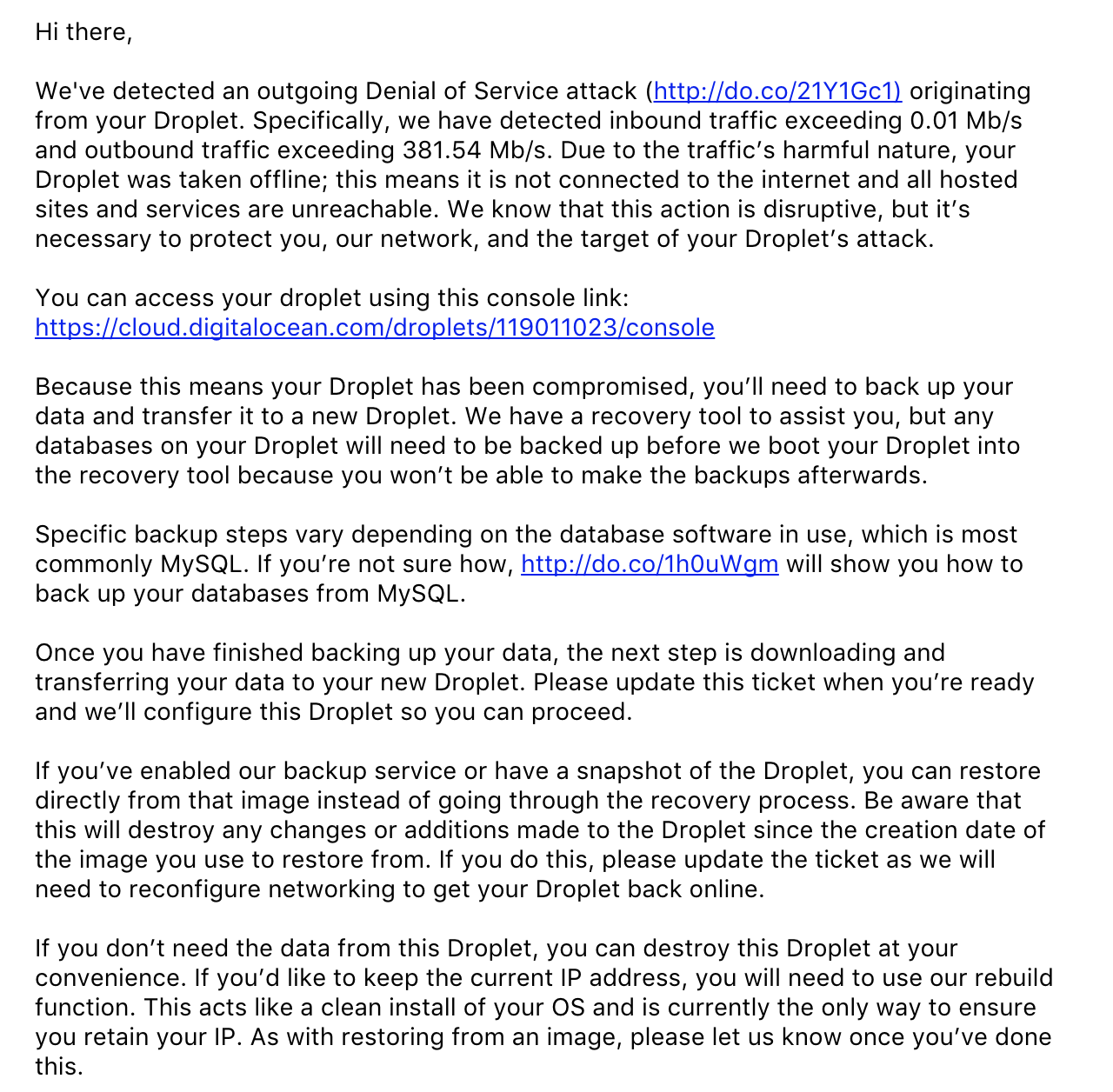
I didn’t set up anything else on the VPS apart from Ghost. I emailed them and asked what happened and how I could understand but they remained very vague in their replies. Is there a way to understand what happened for a novice like myself? This was a test droplet and the root password was rather simple but still bothering to see this happen.
As I said above  try to go through the VPS securing recommendations and you should reduce the risk of having a compromised server. Also, your safest bet is to just create a new droplet, secure it and move your Ghost installation there.
try to go through the VPS securing recommendations and you should reduce the risk of having a compromised server. Also, your safest bet is to just create a new droplet, secure it and move your Ghost installation there.
@Kevin  so it seems the one click install is not that secure after all and truth be told it still depends on the strength of the root password if one was setup vs using a SSH key for a stronger security.
so it seems the one click install is not that secure after all and truth be told it still depends on the strength of the root password if one was setup vs using a SSH key for a stronger security.
I think this is the answer to your issue.
As @dsecareanu said, the weak root password is most likely the problem if you didn’t follow it up with further security measures.
For a more secure DigitalOcean droplet from the get-go it’s always recommended to have uploaded your public SSH key to your DigitalOcean account before creating a droplet. That way the “Add your SSH keys” checkbox for your key is automatically checked on the create page and password login via SSH is disabled which would have prevented a weak password being brute-forced.
I think there are a few things that can be added to the Ubuntu install documentation here:
To help users be more aware of security risks and to streamline the installation process, namely:
Maybe update the DO one click tutorial to factor in the above security steps as well:
https://www.digitalocean.com/docs/one-clicks/ghost/
I know these details might be a bit out of scope, but they shouldn’t take too much space and will ensure that new Ghost users at least are aware of the few steps they could go through to improve their web server security.
My favourite WordPress server setup tutorial is this one and I think it provides a ton of valuable and useful information (I will work on writing a similar detailed one for Ghost CMS in the near future):
This topic was automatically closed 14 days after the last reply. New replies are no longer allowed.